7 Easy Facts About Cyber Security Awareness Shown
Table of ContentsUnknown Facts About Cyber Security Awareness5 Easy Facts About Cyber Security Awareness ShownSome Known Factual Statements About Cyber Security Awareness Cyber Security Awareness - The FactsThe Greatest Guide To Cyber Security Awareness
Aside from work experience and university levels, some employers additionally favor task candidates who have received qualifications demonstrating their understanding of ideal methods in the field. For instance, the Licensed Details Solution Security Expert (CISSP) credential validates a specialist's basic expertise and also capabilities in info safety. There are additionally more particular certifications, which can highlight specific understanding of computer system architecture, design or administration.Cyber safety and security is the technique of protecting computer systems, networks, as well as information from harmful digital strikes. It is typically contrasted with physical security, which is the more conventional safety and security method targeted at regulating accessibility to buildings and various other things in the real world. There are lots of state-of-the-art physical protection strategies, and often physical and also virtual safety and security are collaborated in the org graph under the exact same executive, cyber protection concentrates on safeguarding properties from malicious logins and code, not robberies.
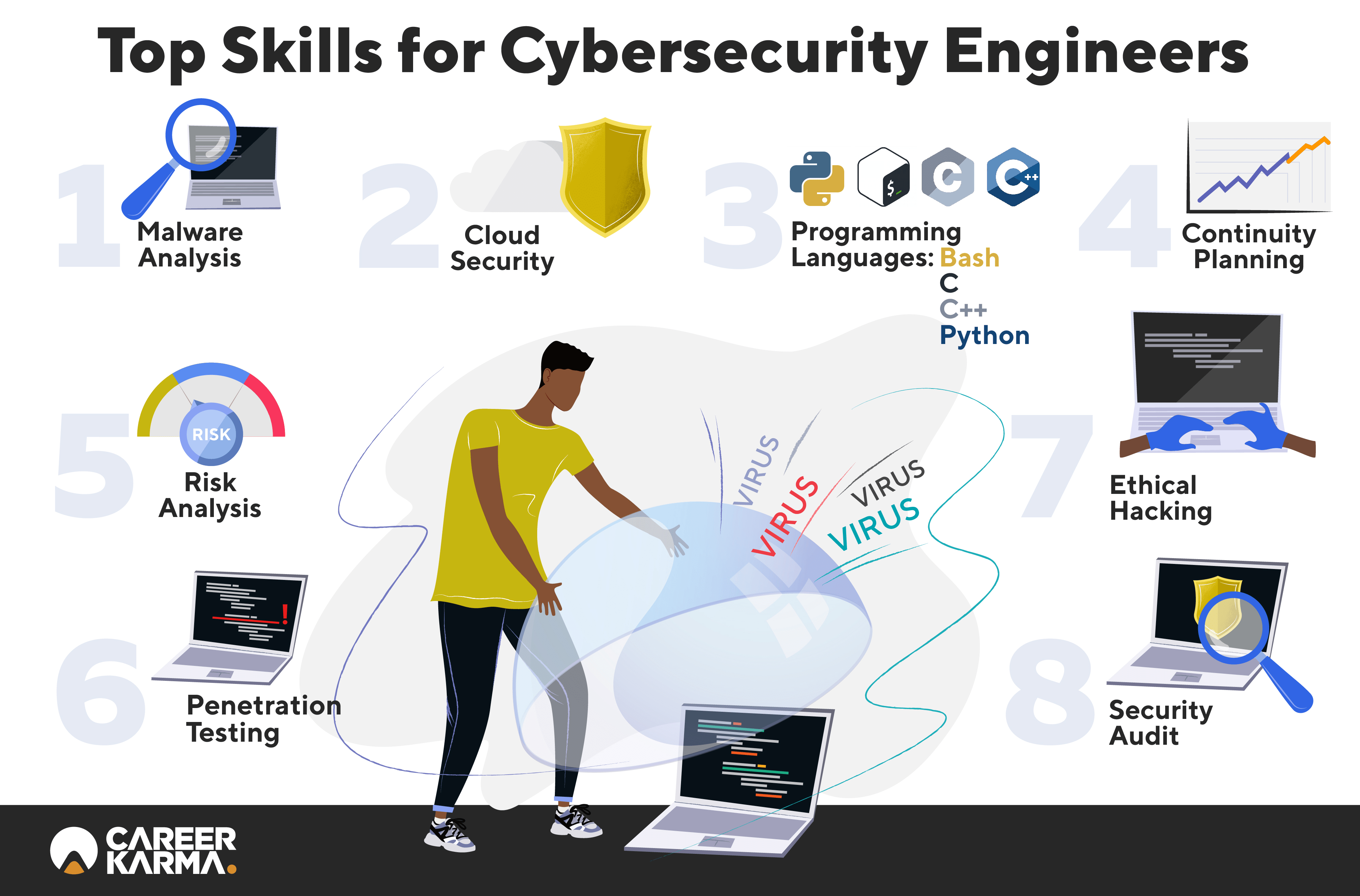
There are a number of methods to break down the different kinds Kapersky Labs has one schema, Mindcore one more yet right here are the most famous kinds you'll read about: prevents and safeguards against unauthorized invasion right into company networks makes applications more secure by finding and repairing susceptabilities in application code occasionally likewise referred to as keeps information protect from unauthorized accessibility or alterations, both when it's being stored and also when it's being sent from one maker to one more often abbreviated as is a procedure whereby organizations analyze and shield public data about themselves that could, if effectively analyzed as well as organized with various other data by a creative enemy, disclose a larger image that ought to stay concealed Some aspects of are likewise taken into consideration to lie under the cyber protection umbrella; specifically, methods to remediate extensive data loss or service blackouts as an outcome of a cyber attack are component of the larger cyber safety self-control Each of the kinds of cyber security battle cyber protection dangers within a particular conceptual world (Cyber Security Awareness).
7 Easy Facts About Cyber Security Awareness Explained
Both HIPAA as well as GDPR, as an example, have comprehensive cyber safety structures mandating certain procedures firms covered by the laws need to comply with. Obviously, a lot of online protection structures are not necessary, even ones established by federal governments. Among one of the most preferred of these is NIST's Cybersecurity Framework, version 1. 1 of which was released in April of 2018.
These real responsibilities can differ widely from company to firm, so it's important to take a more detailed look at each work separately to recognize it. At the really top of the food cycle is the Chief Info Safety Police Officer, or CISO, though even that title isn't set in rock.
Safety and security leaders have elbowed their means right into the C-suite and conference rooms, as securing firm data weblink becomes mission important for companies., and you'll recognize that they link into the kinds of cyber safety and security we noted above.
Not known Details About Cyber Security Awareness
This was specifically true as cyber protection took a while to become an unique technique; several departments developed de facto security pros from within, simply out of individuals who had an interest in the subject. Nonetheless, as is also true of several aspects of IT today, cyber safety and security has become increasingly more professionalized, as well as lots of university courses as well as also majors have actually emerged to prepare possible cyber protection personnel.
The information of cyber security work are, like any type of sophisticated task, constantly altering, and also the secret to proceeding success is to keep learning and also stay flexible: as safety and security evangelist Roger Grimes puts it, "re-invent your skills every 5 to 10 years."One method, though certainly not the only method, to show that you're keeping up with the market is to seek some cyber security qualifications.
The Definitive Guide to Cyber Security Awareness
It is past the scope of this paper to offer all cyber abilities that hazard stars might release. Below is a nonexhaustive listing of usual devices as well as strategies that are utilized by threat actors. For simplicity, they are detailed alphabetically and are not ranked according to regularity or influence - Cyber Security Awareness. [Logiciel try this web-site publicitaire ou publiciel] is brief for advertising and marketing software as well as its primary purpose is to create income by supplying tailored online advertisements.
2 typical code injection strategies are and also. XSS is a code shot technique wherein a threat star infuses and also performs destructive code within a web application by bypassing the mechanisms that verify input. The harmful code is carried out in the browser read what he said of individuals accessing the made use of internet application. Code infused by XSS might either be a single execution or stored for future use.

See This Report on Cyber Security Awareness
g., by means of LDAP or Energetic Directory) so that controls can be provided from one system rather of spread throughout many specific systems. For the numerous medical gadgets that are auto-logon and in continuous use, various other kinds of accessibility controls can be placed in location such as preshared keys and/or MAC address verification.